Mr. Johnson (talk | contribs) No edit summary |
Mr. Johnson (talk | contribs) No edit summary |
||
| (3 intermediate revisions by the same user not shown) | |||
| Line 1: | Line 1: | ||
[[Category:Workflow]][[Category:Matrix Workflow]] | [[Category:Workflow]][[Category:Matrix Workflow]] | ||
The first step in making use of the matrix is getting connected, with or without permission. | The first step in making use of the matrix is getting connected, with or without permission. This article assumes basic familiarity with the [[Matrix Basics|basic layout]] of a {{Tab|Character|Matrix}}. | ||
{{Needs Improvement|Matrix functionality was significantly changed in {{ver|0.30.0|s}}. This section is currently incomplete and does not accurately reflect the current state of the system.}} | {{Needs Improvement|Matrix functionality was significantly changed in {{ver|0.30.0|s}}. This section is currently incomplete and does not accurately reflect the current state of the system.}} | ||
==Legitimate Access== | ==Legitimate Access== | ||
{{Imagebox|sr5-matrix-select_a_network.webp|Select a Network|s=0.30.6|f=13.350|float=right|width=400px}} | {{Imagebox|sr5-matrix-select_a_network.webp|Select a Network|s=0.30.6|f=13.350|float=right|width=400px}} | ||
| Line 22: | Line 20: | ||
* {{Anchor|Host}} | * {{Anchor|Host}} | ||
{{Stub:Roll Dialog Bullets}} | {{Stub:Roll Dialog Bullets}} | ||
If the attempt is successful, the hacker will recieve the selected number of marks on the target Host or Grid, and it will appear on their {{Anchor|Marks Subtab}}. | |||
<div style="display: flex; flex-direction: row; flex-wrap: wrap; justify-content: center;"> | <div style="display: flex; flex-direction: row; flex-wrap: wrap; justify-content: center;"> | ||
<div>{{Imagebox|Sr5-matrix-host-hack-dialog.webp|Hack on the Fly vs. Host Dialog|s=0.30.6|f=13.350|float=none|width=224px}}</div> | <div>{{Imagebox|Sr5-matrix-host-hack-dialog.webp|Hack on the Fly vs. Host Dialog|s=0.30.6|f=13.350|float=none|width=224px}}</div> | ||
<div>{{Imagebox|Sr5-matrix-host-hack-rollcard.webp|Hack on the Fly vs. Host Rollcard|s=0.30.6|f=13.350|float=none|width= | <div>{{Imagebox|Sr5-matrix-host-hack-rollcard.webp|Hack on the Fly vs. Host Rollcard|s=0.30.6|f=13.350|float=none|width=292px}}</div> | ||
<div>{{Imagebox|Sr5-matrix-host-resist-rollcard.webp|Host Resistance Rollcard|s=0.30.6|f=13.350|float=none|width= | <div>{{Imagebox|Sr5-matrix-host-resist-rollcard.webp|Host Resistance Rollcard|s=0.30.6|f=13.350|float=none|width=292px}}</div> | ||
</div> | </div> | ||
{{References}} | {{References}} | ||
Latest revision as of 20:34, 7 October 2025
The first step in making use of the matrix is getting connected, with or without permission. This article assumes basic familiarity with the basic layout of a Character's Matrix Tab.
This article was last edited Tuesday, October 7, 2025 by Mr. Johnson.
Legitimate Access
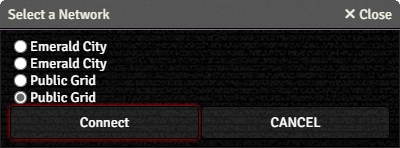
Hosts and Grids a character has legitimate access to can be added to one of the Actor's SINs, and they will show up under the Direct Connect Network button. The character can connect to these networks without any Test. Connecting to one will change the label to indicate which one they're connected to and show a button to disconnect.
The example to the right shows duplicate entries because the character has the same grid access from two different SINs. If accessed from a GM login, it will show every Host and Grid present in the sidebar.
Illicit Access
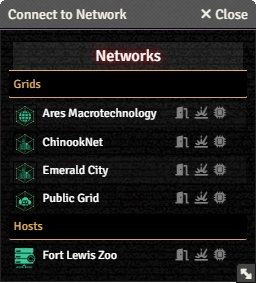
Systems the character does not have unlimited permission to access can be viewed by the Mark Network button. This dialog box shows all the Grids and Hosts that have the Visible flag enabled.
Each Grid and Host will listed with three buttons:
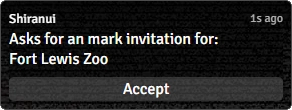
- allows the character to ask for an invitation[sr 1], and will prompt the GM to approve it.
- will initiate a Brute Force[sr 2] attack to gain marks.
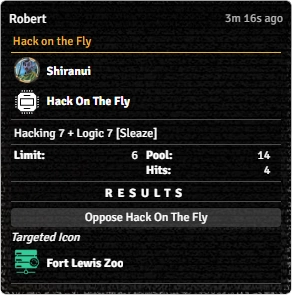
- will initiate a Hack on the Fly[sr 3] attempt to gain marks.
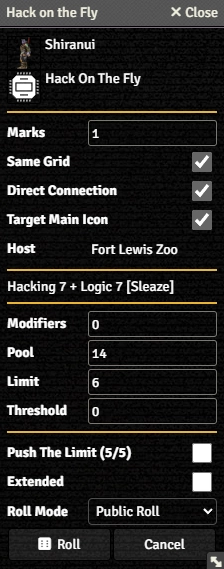
Selecting either of the latter two options will present the appropriate roll dialog, with multiple options to configure the attempt:
- Marks allows the hacker to declare the number of marks they're going for (1 to 3), and applies the appropriate penalty to the test. For Qualities like Go Big Or Go Home[sr 4], Active Effects can adjust the modifier by targetting
system.modifiers.place_two_marksorsystem.modifiers.place_three_marks. - Direct Connection
- Target Main Icon
- Host
- The next line shows a summary of the Skill, Attribute, and other modifiers included in the roll, plus the Limit.
- Modifiers, Pool, Limit, and Threshold show the calculated values for the Test. They can be maually modified.
- Push The Limit[sr 5] shows the Actor's current and maximum Edge, and provides a checkbox to apply it to the current attack.
- Roll Mode applies one of Foundry's Roll Modes whenever the action is used. It overrides whatever is selected in the Chat Messages sidebar.
- Pressing Roll executes the roll.
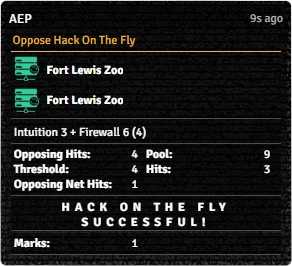
If the attempt is successful, the hacker will recieve the selected number of marks on the target Host or Grid, and it will appear on their Marks Subtab.
References
Sourcebook
- ↑ Shadowrun Fifth Edition Core Rulebook (p. 236)
- ↑ Shadowrun Fifth Edition Core Rulebook (p. 238)
- ↑ Shadowrun Fifth Edition Core Rulebook (p. 240)
- ↑ Data Trails (p. 44)
- ↑ Shadowrun Fifth Edition Core Rulebook (p. 56)